The number of phishing mails has risen since corona and the messages are getting better and more advanced, reports the TU Delft Security Team. How can you protect yourself?
“Phishing mails getting better and more advanced.” (Illustration: Design by Freepik)
Phishing is a type of digital fraud with which criminals try to obtain sensitive information such as banking and login details. It is a growing problem. Since the corona crisis, the TU Delft Security Team has seen a rise in the number of phishing mails sent to students and staff. This trend is clear to see in a Proofpoint report. Proofpoint is the email filter that checks the links in emails originating from external sources and on all the devices that staff use.
“Fortunately, the email filter catches many of these fraudulent emails so staff and students do not have too many problems,” says the recently appointed Chief Information Security Officer, Jérôme Zijderveld. “But everyone still has to stay alert as phishing is a real cat and mouse game.”
Of the emails that do manage to get through the filter, the Security Team requests that these be sent to abuse@tudelft.nl, the email address where students and staff report suspicious online activity.
Awareness training
But how can you recognise phishing and other types of online fraud? To help its staff and students become more digitally adept, TU Delft has recently started a pilot involving security awareness training. “Two hundred staff members and a few students are taking part in the pilot in three groups,” says Zijderveld. “This will help us see the types of training that we need to run at TU Delft.”
As part of the pilot, one of the groups received a phishing mail at the end of April. The email, disguised as an information message about a change in the social media policy, was sent under the name of former Human Resources Director Ingrid Halewijn who left on 1 April. The message contained a PDF attachment. Anyone opening the PDF saw the following message:
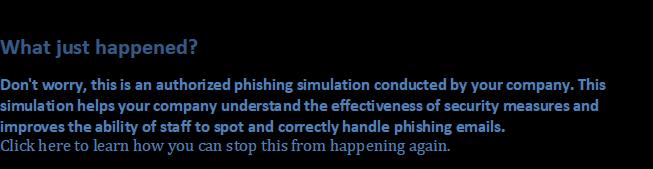

Phishing mails sent under the name of TU Delft staff members is nothing new. It confirms the idea that this form of internet criminality is becoming better and more advanced. “Obtaining information about an organisation through social engineering is becoming more common,” says Zijderveld. Social engineering is a technique through which internet criminals obtain confidential information through the weakest link (humans). To do this, criminals pretend to be someone in the organisation. They take their time to make contact, gain the trust of the staff member and then fish for information.
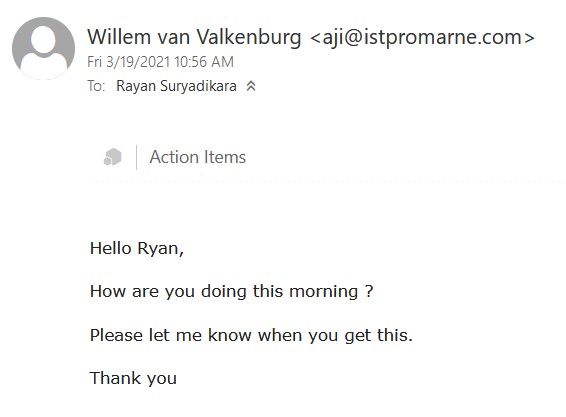

Delta’s intern received a mail like this. It was a message sent under the name of Willem van Valkenburg, Chair of the Exam Taskforce. As the email address of the sender was not linked to TU Delft in any way, it was immediately clear that it was not a message from the ‘real’ Willem van Valkenburg. We need to be alert, says Zijderveld. “In the case of advanced ‘social engineering’, the real TU Delft email address can be ‘spoofed’ so that it is harder to recognise it as false.”
As yet, these new techniques have not led to major incidents. “However,” says Zijderveld, “ransomware has been found on some computers, though it had no significant consequences. No ransom money was paid either.”
How do you recognise a phishing mail?
- Check for spelling mistakes in the email.
- The email is often not addressed personally. It may be addressed to ‘Dear contact’ or ‘Dear customer’ for example. That said, even if you are addressed by name personally, you still may be a victim of phishing.
- It usually asks for action to be taken quickly. You may be asked to pay something fast for example.
- The email comes from an odd email address. The part after the @ can reveal the origin of an email. Emails originating from TU Delft end in ‘tudelft.nl’.
- The links in the email are to strange looking web addresses. Check this by moving your mouse onto a link in the email without clicking. You will then see the web address in a small pop-up notice or right at the bottom of the screen. TU Delft works with a protection mechanism: URL rewrite. If the URL starts with https://urldefense.proofpoint.com, you can click on the link. If the URL is recognised as suspicious, it will be blocked by this mechanism. Even if the URL is not blocked, it is still important to carefully check the URL that is in the address bar of the browser. It is always advisable to check the URL carefully, especially those for login pages (even those from TU Delft).
- You may be asked to open programmes or documents that are sent in the email. These attachments could contain malware or viruses that automatically send you to an online phishing form.
- Be alert if someone asks you to do something or to click on something.
- Be very careful with suspicious messages in which your personal details are asked for. Never respond to these suspicious messages and never click on the links in the messages and never open the attachments or downloads in the message. Instead, send the message to abuse@tudelft.nl so that a report can be done and it can be checked if it really is a phishing email.
- Send every suspicious email to abuse@tudelft.nl.
Warning for CEO Fraud
TU Delft also requests its staff to be aware of CEO fraud. This is a form of abuse in which someone pretends to be a colleague or supervisor and asks for money to be transferred. Criminals often use email addresses such as name.surname.tudelft@hotmail.com. These emails have no links and thus get through the filter easily. Examples of these emails are requests for payment or the purchase of a gift token. According to Zijderveld, “TU Delft will never ask you to transfer money or to buy gift tokens. If you receive this type of request, report it immediately to abuse@tudelft.nl.”
How do you recognise CEO fraud?
- The sender uses other communication channels than the standard ones such as a hotmail or a gmail address, or sends an SMS.
- The sender emphasises a position of authority and orders payment.
- As the receiver, you may be praised or told that you are important. You have been chosen to do the task because of your exceptional qualities. The success of the projects lies in your hands.
- The sender often emphasises that it is a one-time payment that needs you to ignore the standard procedure.
- The sender emphasises the important of confidentiality. The receiver may not share the order with colleagues.
- The receiver must make the payment fast.
llustration: Design by Freepik
Do you have a question or comment about this article?
m.vanderveldt@tudelft.nl


Comments are closed.